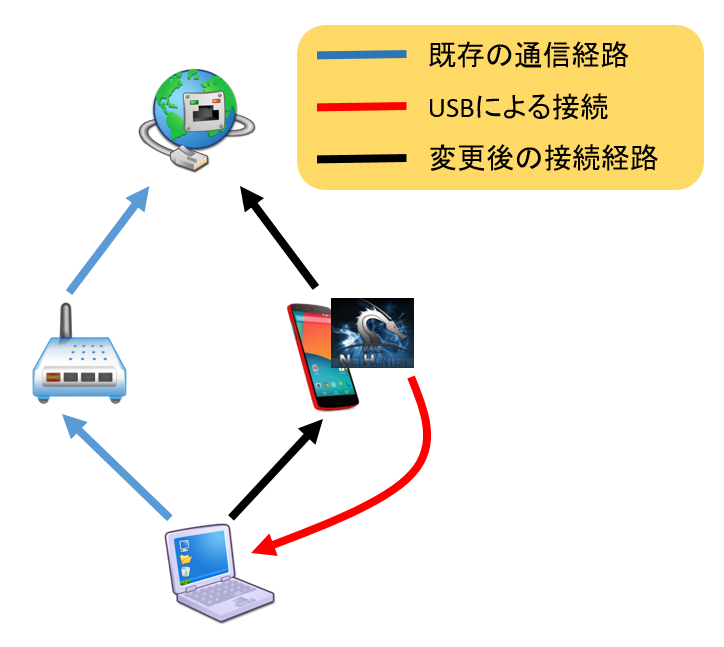
The MitM devices used in this paper. Top: Three 1Gbps Ethernet switches... | Download Scientific Diagram

Ingecom distribuye las llaves de seguridad de autenticación por hardware de Yubico | Actualidad | IT Digital Security
GitHub - BenGardiner/USBProxy: A USB man in the middle device using USB On-The-Go, libUSB and gadgetFS

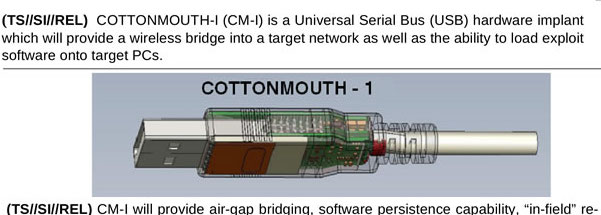
BadUSB 2.0 USB MITM POC. – Security List Network™ | Computer security, Cyber security, Hacking computer

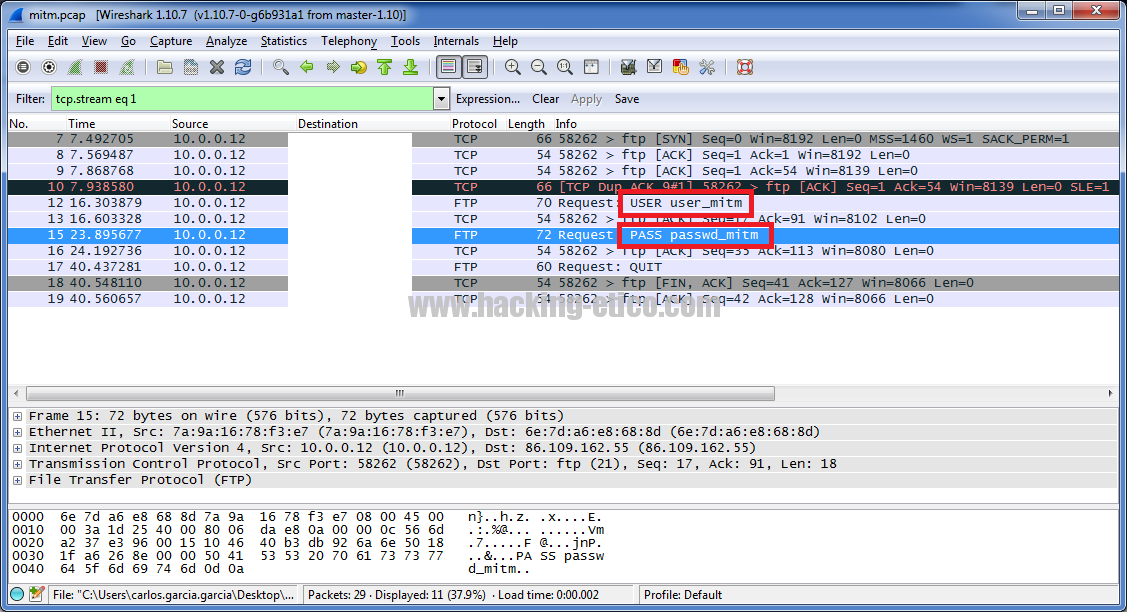
Owning the Network with BadUSB. Man-in-the-Middle with a Raspberry Pi | by Jacob Baines | Tenable TechBlog | Medium

keylogger Memoria USB/Teclado para PC de supervisión (KeyGrabber USB 16 MB) para Mac, Linux, Windows : Amazon.es: Informática




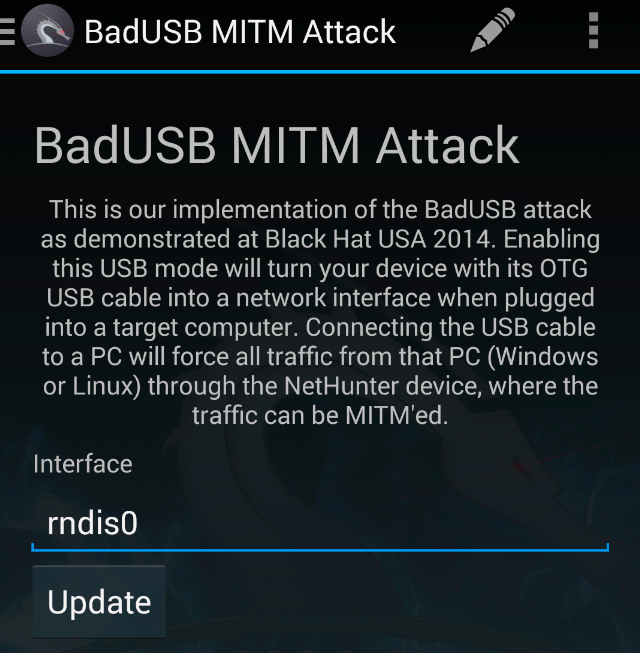
![PDF] BadUSB 2 . 0 : USB man in the middle attacks | Semantic Scholar PDF] BadUSB 2 . 0 : USB man in the middle attacks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/907e8c34507e1d78f048abb26fa9c684097a562c/19-Figure3.1-1.png)